Let’s face it USB drives can come in handy, even in a connected world. Sometimes that thumb drive is the easiest way to bring a large file you worked on at home back to the office. Or, even downloading an update specific to your equipment from a vendor. However, as convenient as a USB drive can be, it can also put an organization on a slippery slope where vulnerabilities can run rampant and open doors to outside parties.
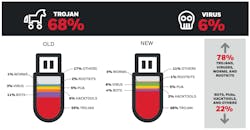
Honeywell recently released its Industrial USB Threat Report, examining data collected from hundreds of industrial facilities globally using Honeywell’s Secure Media Exchange (SMX) technology. The report reveals that the severity of threats detected to operational technology (OT) systems has risen significantly over a 12-month period:
Obviously, the danger of thumb drives has been on the enterprise radar for a while now. But, why do these trends matter to manufacturers? Simply put, USB removable media is often a necessity in OT, and because of that it’s becoming an increasingly utilized vector, explains report author Eric Knapp, director of Cybersecurity Research and engineering fellow, Honeywell Connected Enterprise, Cybersecurity. “Manufacturers first need to understand the scope of this vector, and if they aren’t already doing so, they should include removable media in their security strategy,” says Knapp. “Many organizations have policies in place around the use of removable media, but USB is now so ubiquitous that devices will find their way into industrial control and automation environments, so policies alone aren’t enough. With threats becoming more focused with higher impact, controls need to be put in place to enforce those policies.”
Knapp tells IndustryWeek, there are some best practices manufacturers can embrace to help improve these environments.
First, removable media shouldn’t be dismissed outright. “Trying to disable USB entirely would be like trying to establish a true air gap: first, you’re not likely to succeed, because the technology engrained in our lives and our businesses; second, even if you did succeed the attackers would just find another way in,” says Knapp. “As such, organizations should strive to understand the applicable vectors into OT and securing them as much as possible.”
According to Knapp, removable media should be considered from a few angles. “It’s not just about a thumb drive. There’s the drive itself, the files contained on that drive, the USB port on the end node that the drive connects to, and the USB protocols that let everything interact together. At a minimum, removable media should be scanned for malware,” he says. “However, to be considered ‘best practice’ all these pieces need to be considered. For example, can a user bypass the scanning process and connect directly to an end node? Is the thumb drive itself a source of threat? How do you enforce what USB devices are even allowed to connect, and once connected, how are the contents of that drive accessed? If you approach removable media like any other data flow, you’ll be able to answer these questions and in turn reduce the risk of using USB.”
About the Author
Peter Fretty
Technology Editor
As a highly experienced journalist, Peter Fretty regularly covers advances in manufacturing, information technology, and software. He has written thousands of feature articles, cover stories, and white papers for an assortment of trade journals, business publications, and consumer magazines.