The threat landscape is expanding as IT and OT networks converge, understandably putting manufacturing organizations at risk. According to a recent IoT Analytic’s report, 50% of industrial assets in factories will be connected to some form of on-premise or remote data collection system. Unfortunately, many OT systems were never designed for remote or internet access. As such, connectivity risks were not fully considered.
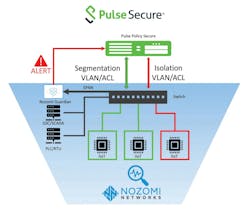
To address this growing issue, Pulse Secure and Nozomi Networks, recently announced an integration to extend the zero trust protection to industrial IoT, ICS and OT technologies. The goal is to help address critical cybersecurity challenges as IT and OT rapidly merge, and protects OT, ICS and IIoT infrastructure so organizations can securely bring IIoT devices from their classical OT isolation into the IT realm to increase operational flexibility, reduce time for troubleshooting and improve overall uptime and productivity.
“While the convergence of IT and OT offers benefits of improved efficiencies, it also exposes previously isolated systems to cyberattacks. As OT devices are connecting beyond their traditional silos, device visibility, understanding and defenses are rising in importance,” said Tony Massimini, senior industry analyst for network security at Frost & Sullivan. "Critical OT, ICS and IIoT systems if left unchecked are often vulnerable to cyberattacks, which urges security professionals to explore solutions that provide integrated discovery, monitoring, provisioning and threat response. The Nozomi Networks and Pulse Secure solution expands on the foundational capabilities of a Network Access Control (NAC) solution to enable secure, controlled IT/OT connectivity for devices, as well as remote administration and support services."
Pulse Secure Vice President of Product Management Prakash Mana tells IndustryWeek, “Manufacturing and other enterprises want to be able to bring in more advanced security systems in a way that is least intrusive and works with their existing on-premise and cloud infrastructure. Ease of implementation and investment protection is key.”
According to Mana, the cornerstone of IIOT 4.0 is IT/OT convergence to enable more flexible management, easier monitoring and analytics, and faster response to address outage and capacity issues. “However, opening up once closed systems to enterprise networks and the internet requires increased security measures - access manage and operational intelligence are foundational controls for security and compliance,” he says. “Numerous cases of security exposures and successful cyberattacks have made IoT/IIoT security an imperative as most of these devices do not have embedded security features or are unable or have poorly maintained system hygiene – leaving them vulnerable to disruption or compromise.”
Digging deeper
The joint solution automates the discovery and classification of a broad range of IIoT devices and affords continuous monitoring and response to anomalous and malicious events. “In addition, Pulse Secure can control remote and on-premise privileged user and service technician access to expedite maintenance, diagnostics and service resumption while mitigating access threats such as insecure or unsanctioned device use,” says Mana.
Pulse Secure’s open platform approach facilitates integration with IIoT security solutions, like those from Nozomi Networks, and are purpose-built to roll out zero trust environments without impeding user experience or productivity.
“Attackers increasingly use connectivity and IoT device exposures to scan the network for other exploitable targets that provide access to sensitive data or credentials as well as enable operational disruption. Pulse Secure’s NAC solution provides the necessary visibility and policy-based access management to ensure appropriate IoT device onboarding, monitoring, segregation and risk mitigation,” said Mana. “By integrating with Nozomi Networks, we can further extend native operational intelligence, access control and threat response capabilities of IIoT devices operating within OT and ICS environments.”
“As IT and OT networks become more interconnected, the attack surface for cyber threats has expanded and is creating greater risk for the entire organization,” said Nozomi Networks Co-founder and CPO Andrea Carcano. “This integration with the Pulse Secure Access Suite, allows customers to leverage Nozomi Networks solutions to extend Pulse Secure’s zero trust protections across industrial IoT, ICS and OT networks.”
About the Author
Peter Fretty
Technology Editor
As a highly experienced journalist, Peter Fretty regularly covers advances in manufacturing, information technology, and software. He has written thousands of feature articles, cover stories, and white papers for an assortment of trade journals, business publications, and consumer magazines.